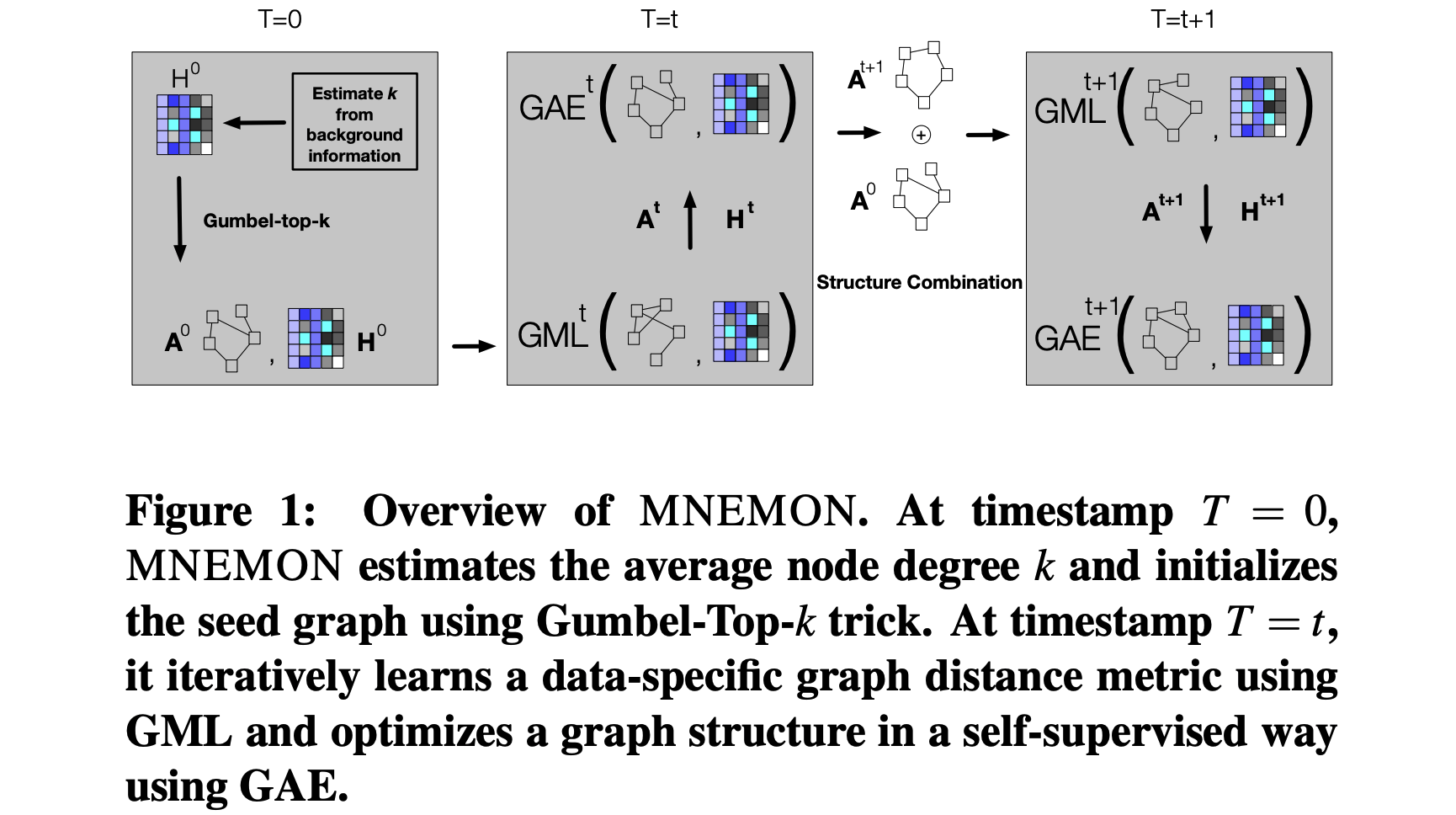
Abstract
Previous security research efforts orbiting around graphs have been exclusively focusing on either (de-)anonymizing the graphs or understanding the security and privacy issues of graph neural networks. Little attention has been paid to understand the privacy risks of integrating the output from graph embedding models (e.g., node embeddings) with complex downstream machine learning pipelines. In this paper, we fill this gap and propose a novel model-agnostic graph recovery attack that exploits the implicit graph structural information preserved in the embeddings of graph nodes. We show that an adversary can recover edges with decent accuracy by only gaining access to the node embedding matrix of the original graph without interactions with the node embedding models. We demonstrate the effectiveness and applicability of our graph recovery attack through extensive experiments.
Citation
@inproceedings{SHZCYBZS22,
author = {Yun Shen and Yufei Han and Zhikun Zhang and Min Chen and Ting Yu and Michael Backes and Yang Zhang and Gianluca Stringhini},
title = {{Finding MNEMON: Reviving Memories of Node Embeddings}},
booktitle = {{ACM CCS}},
publisher = {},
year = {2022},
}





